I have administered Unix/Linux systems for over 40 years now. For the last 25 or more, I’ve been very interested in automation and repeatable configuration. I started playing around with cfengine in the late 1990s as a tool to make it easier to administer a large number of systems with a small number of admins. Recently, I’ve used ansible for that due to issues with having to do push rather than pull (firewalls that won’t allow systems to reach back “inside” to get updates).
For the last 15 years or so, I’ve administered a lot of Ubuntu systems for my own personal use (and also at various paid and unpaid jobs). At a few previous jobs, I would schedule change windows every quarter to apply patch bundles, and that worked in those environments, but it meant the critical patches either didn’t necessarily get applied in a timely fashion or required emergency change controls. Okay, for systems that require 24×7 uptime, that is an issue anyway, but many of the systems I’ve managed over the years, could afford a few minutes of downtime in the middle of the night without anyone really noticing. I’m a big fan of Debian/Ubuntu’s unattended-upgrades, a package that allows the systems/servers to download (and potentially apply) upgrades on their own every night. Whether or not I allow the reboots every night depends on the system (and whether I’m working any cases at the time).
To get back to the actual point of this post, when I add packages that don’t come from the standard repositories, I add them to the /etc/apt/sources.list.d/ directory which works fine for the initial installation, but doesn’t necessarily add them to the packages that get the automatic treatment from unattended-upgrades. Somewhere over the last few years, I found a post somewhere (I have no idea where, my attempts to find it again have been spectacular failures). So, I figured I’d write it down here because if I don’t do it for a while, I forget the command line. So, if I want to have the new package automatically upgrade as new versions are released I need to add the package to the Unattended-Upgrade::Allowed-Origins in /etc/apt/apt.conf.d/50unattended-upgrades (or add a 99local or similar to that directory). The problem that I’ve had is figuring out exactly what needs to go into the allowed origins section. So (wherever it was that I found it before), the magic is using the apt-cache policy command to figure out the magic.
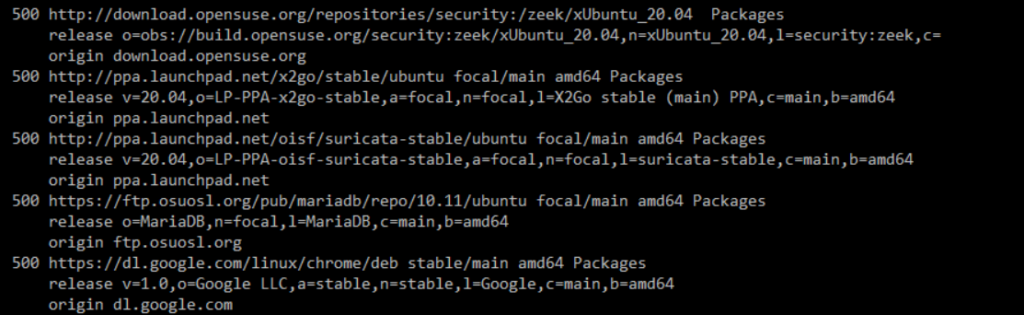
And the answer is in that release line. What I need is the o= and a= pieces. So I actually, just run apt-cache policy | grep -i release (I actually, used to grep for the o= and a=, too, but since those only appear on the release line, that grep was redundant) and find what I need
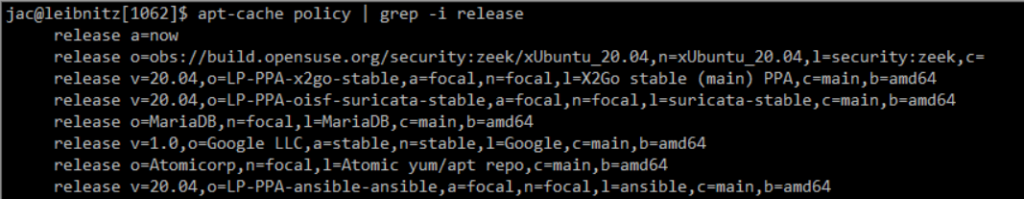
Then I take the o= and a= parts and add them to the Unattended-Upgrade::Allowed-Origins. So, I have the following
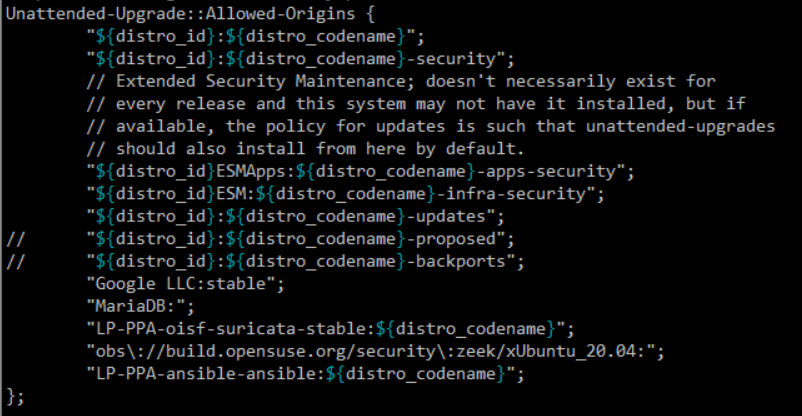
Or, in most cases I add that to an ansible playbook that I then apply to all the systems of that type, so that I can maintain the consistent configurations. And, there you have it (and I can find it again the next time).